How To Check If My Https Certificate Is Registered For Both Www And Non Www
This browser is no longer supported.
Upgrade to Microsoft Border to take advantage of the latest features, security updates, and technical support.
Add a TLS/SSL document in Azure App Service
Azure App Service provides a highly scalable, self-patching web hosting service. This article shows you how to create, upload, or import a individual certificate or a public certificate into App Service.
Once the certificate is added to your App Service app or part app, you can secure a custom DNS name with it or use it in your application code.
Note
A certificate uploaded into an app is stored in a deployment unit that is bound to the app service plan's resource grouping, region and operating system combination (internally called a webspace). This makes the certificate accessible to other apps in the same resource group and region combination.
The following table lists the options you accept for adding certificates in App Service:
| Option | Description |
|---|---|
| Create a free App Service managed certificate | A private certificate that's gratuitous of charge and easy to use if y'all just need to secure your custom domain in App Service. |
| Buy an App Service certificate | A private certificate that'south managed past Azure. Information technology combines the simplicity of automated certificate management and the flexibility of renewal and consign options. |
| Import a document from Key Vault | Useful if you use Azure Fundamental Vault to manage your PKCS12 certificates. Run into Private document requirements. |
| Upload a private certificate | If you already have a private certificate from a third-political party provider, you can upload it. See Individual document requirements. |
| Upload a public document | Public certificates are not used to secure custom domains, but you tin load them into your code if y'all need them to access remote resources. |
Prerequisites
- Create an App Service app.
- For a individual certificate, make sure that information technology satisfies all requirements from App Service.
- Gratuitous certificate only:
- Map the domain you lot desire a certificate for to App Service. For information, run into Tutorial: Map an existing custom DNS proper name to Azure App Service.
- For a root domain (similar contoso.com), make sure your app doesn't have whatsoever IP restrictions configured. Both certificate creation and its periodic renewal for a root domain depends on your app being reachable from the net.
Private document requirements
The free App Service managed document and the App Service certificate already satisfy the requirements of App Service. If you choose to upload or import a individual document to App Service, your document must meet the following requirements:
- Exported as a password-protected PFX file, encrypted using triple DES.
- Contains individual key at to the lowest degree 2048 bits long
- Contains all intermediate certificates and the root certificate in the certificate concatenation.
To secure a custom domain in a TLS binding, the certificate has boosted requirements:
- Contains an Extended Key Usage for server hallmark (OID = 1.three.6.1.five.5.seven.three.one)
- Signed by a trusted certificate authority
Note
Elliptic Curve Cryptography (ECC) certificates can work with App Service simply are not covered past this article. Work with your certificate authority on the exact steps to create ECC certificates.
Prepare your web app
To create custom TLS/SSL bindings or enable client certificates for your App Service app, your App Service plan must exist in the Basic, Standard, Premium, or Isolated tier. In this step, yous brand sure that your web app is in the supported pricing tier.
Sign in to Azure
Open the Azure portal.
Navigate to your spider web app
Search for and select App Services.

On the App Services folio, select the name of your web app.

You have landed on the management page of your web app.
Check the pricing tier
In the left-manus navigation of your web app page, scroll to the Settings department and select Calibration upwardly (App Service plan).

Check to make sure that your web app is non in the F1 or D1 tier. Your web app's current tier is highlighted by a night blue box.

Custom SSL is non supported in the F1 or D1 tier. If y'all need to scale up, follow the steps in the adjacent department. Otherwise, close the Scale up page and skip the Scale up your App Service programme section.
Scale upwards your App Service plan
Select whatsoever of the non-complimentary tiers (B1, B2, B3, or any tier in the Production category). For additional options, click Run into boosted options.
Click Apply.

When y'all see the following notification, the scale operation is complete.

Create a gratis managed certificate
Note
Before creating a free managed certificate, make sure you have fulfilled the prerequisites for your app.
The complimentary App Service managed certificate is a turn-fundamental solution for securing your custom DNS proper noun in App Service. Information technology'due south a TLS/SSL server certificate that'south fully managed by App Service and renewed continuously and automatically in six-month increments, 45 days before expiration, as long every bit the prerequisites set-up remain the aforementioned without any activity required from you. All the associated bindings will be updated with the renewed certificate. You create the document and bind it to a custom domain, and allow App Service practise the rest.
Important
Because Azure fully manages the certificates on your behalf, any aspect of the managed certificate, including the root issuer, tin can be changed at someday. These changes are outside of your control. You should avoid having a difficult dependency or practise document "pinning" to the managed document, or to any part of the document hierarchy. If y'all demand the document pinning behavior, add a certificate to your custom domain using any other available method in this article.
The complimentary certificate comes with the following limitations:
- Does not support wildcard certificates.
- Does not support usage equally a client certificate by using certificate thumbprint (removal of certificate thumbprint is planned).
- Does not support private DNS.
- Is not exportable.
- Is not supported on App Service Surround (ASE).
- Only supports alphanumeric characters, dashes (-), and periods (.).
- Noon domain
- Subdomain
- Must have an A record pointing to your web app's IP address.
- Is not supported on apps that are not publicly attainable.
- Is not supported with root domains that are integrated with Traffic Manager.
- All the above must exist met for successful certificate issuances and renewals.
Note
The complimentary document is issued by DigiCert. For some domains, you lot must explicitly let DigiCert as a document issuer by creating a CAA domain record with the value: 0 result digicert.com.
In the Azure portal, from the left card, select App Services > <app-name>.
From the left navigation of your app, select TLS/SSL settings > Private Key Certificates (.pfx) > Create App Service Managed Document.
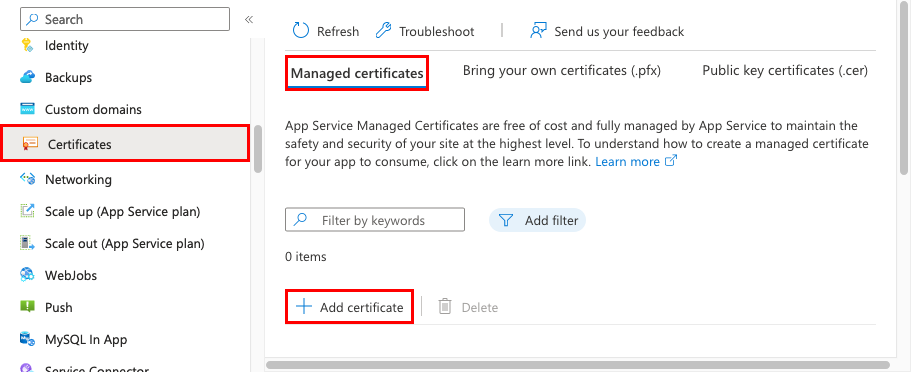
Select the custom domain to create a free certificate for and select Create. You lot tin can create only one document for each supported custom domain.
When the performance completes, you come across the certificate in the Private Fundamental Certificates list.
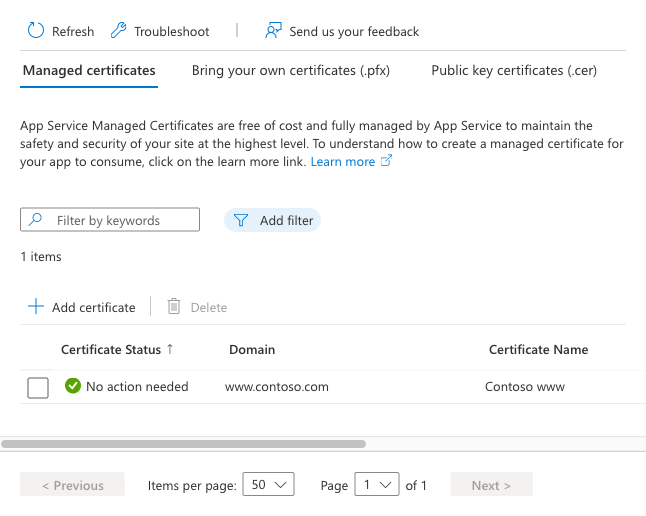
Of import
To secure a custom domain with this document, you still need to create a certificate binding. Follow the steps in Create binding.
Import an App Service Document
If you buy an App Service Certificate from Azure, Azure manages the post-obit tasks:
- Takes care of the purchase process from GoDaddy.
- Performs domain verification of the document.
- Maintains the certificate in Azure Primal Vault.
- Manages certificate renewal (see Renew certificate).
- Synchronize the certificate automatically with the imported copies in App Service apps.
To purchase an App Service certificate, go to Start certificate order.
If you already have a working App Service certificate, you can:
- Import the certificate into App Service.
- Manage the certificate, such as renew, rekey, and export it.
Note
App Service Certificates are non supported in Azure National Clouds at this time.
Commencement certificate order
Start an App Service document order in the App Service Document create page.
Note
All prices shown are for examples merely.

Apply the following table to help y'all configure the document. When finished, click Create.
| Setting | Description |
|---|---|
| Subscription | The subscription that volition contain the certificate. |
| Resources group | The resource group that volition comprise the certificate. You tin employ a new resource group or select the same resource group equally your App Service app, for example. |
| SKU | Determines the blazon of certificate to create, whether a standard certificate or a wildcard certificate. |
| Naked Domain Host Name | Specify the root domain here. The issued certificate secures both the root domain and the www subdomain. In the issued document, the Common Name field contains the root domain, and the Subject Alternative Name field contains the www domain. To secure whatever subdomain just, specify the fully qualified domain name of the subdomain hither (for example, mysubdomain.contoso.com). |
| Certificate name | A friendly name for your App Service certificate. |
| Enable machine renewal | Select whether the certificate should be renewed automatically earlier it expires. Each renewal extends the certificate expiration by ane year and the cost is charged to your subscription. |
Note
App Service Certificates purchased from Azure are issued by GoDaddy. For some domains, you must explicitly let GoDaddy every bit a certificate issuer past creating a CAA domain tape with the value: 0 upshot godaddy.com
Shop in Azure Key Vault
One time the document purchase process is complete, in that location are few more than steps you lot need to complete earlier y'all can starting time using this certificate.
Select the certificate in the App Service Certificates page, so click Document Configuration > Step ane: Store.
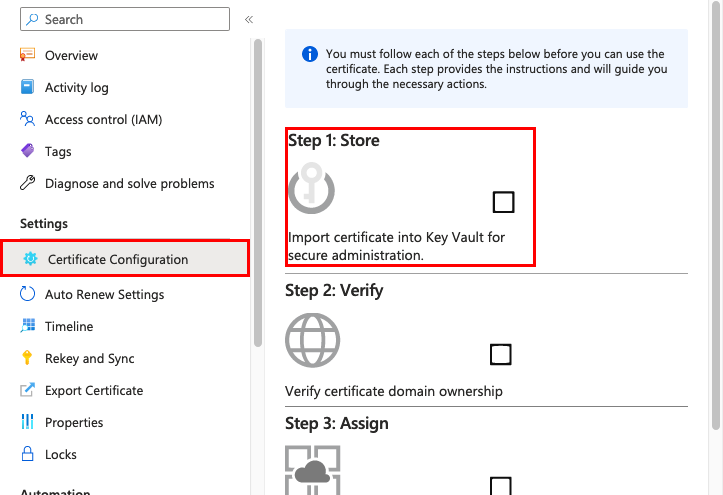
Fundamental Vault is an Azure service that helps safeguard cryptographic keys and secrets used past cloud applications and services. Information technology's the storage of choice for App Service certificates.
In the Cardinal Vault Status folio, click Key Vault Repository to create a new vault or choose an existing vault. If y'all choose to create a new vault, use the post-obit table to assist you configure the vault and click Create. Create the new Key Vault inside the same subscription and resource grouping as your App Service app.
| Setting | Clarification |
|---|---|
| Name | A unique proper noun that consists for alphanumeric characters and dashes. |
| Resources grouping | As a recommendation, select the aforementioned resource group every bit your App Service document. |
| Location | Select the same location as your App Service app. |
| Pricing tier | For information, see Azure Key Vault pricing details. |
| Access policies | Defines the applications and the allowed access to the vault resources. You tin configure it later, post-obit the steps at Assign a Key Vault access policy. |
| Virtual Network Access | Restrict vault access to sure Azure virtual networks. You can configure it afterward, following the steps at Configure Azure Key Vault Firewalls and Virtual Networks |
Once you lot've selected the vault, shut the Key Vault Repository page. The Footstep 1: Store choice should bear witness a green check mark for success. Keep the page open for the adjacent pace.
Note
Currently, App Service Document just supports Key Vault access policy just non RBAC model.
Verify domain buying
From the same Document Configuration page you used in the last step, click Footstep 2: Verify.
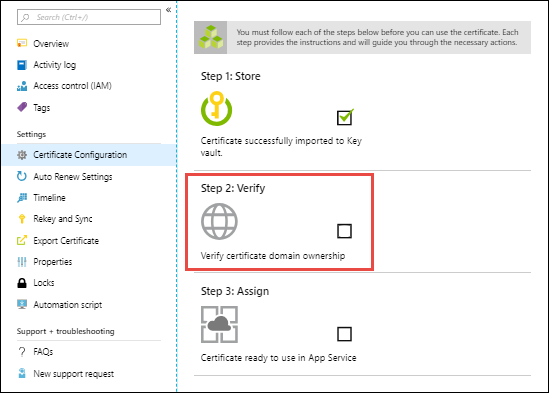
Select App Service Verification. Since yous already mapped the domain to your web app (run across Prerequisites), it's already verified. Just click Verify to finish this stride. Click the Refresh push button until the bulletin Certificate is Domain Verified appears.
Important
For a Standard certificate, the certificate provider gives you a certificate for the requested meridian-level domain and its world wide web subdomain (for example, contoso.com and www.contoso.com). Yet, first on December one, 2021, a restriction is introduced on the App Service and the Transmission verification methods. Both of them utilize HTML folio verification to verify domain ownership. With this method, the document provider is no longer allowed to include the world wide web subdomain when issuing, rekeying, or renewing a certificate.
The Domain and Mail verification methods continue to include the world wide web subdomain with the requested superlative-level domain in the document.
Note
Four types of domain verification methods are supported:
- App Service - The well-nigh user-friendly choice when the domain is already mapped to an App Service app in the aforementioned subscription. It takes advantage of the fact that the App Service app has already verified the domain ownership (see previous note).
- Domain - Verify an App Service domain that yous purchased from Azure. Azure automatically adds the verification TXT record for you and completes the procedure.
- Mail - Verify the domain past sending an email to the domain administrator. Instructions are provided when you select the selection.
- Manual - Verify the domain using either an HTML page (Standard certificate only, see previous notation) or a DNS TXT record. Instructions are provided when y'all select the option. The HTML page choice doesn't work for web apps with "Https Only" enabled.
Import certificate into App Service
In the Azure portal, from the left carte du jour, select App Services > <app-name>.
From the left navigation of your app, select TLS/SSL settings > Private Key Certificates (.pfx) > Import App Service Certificate.
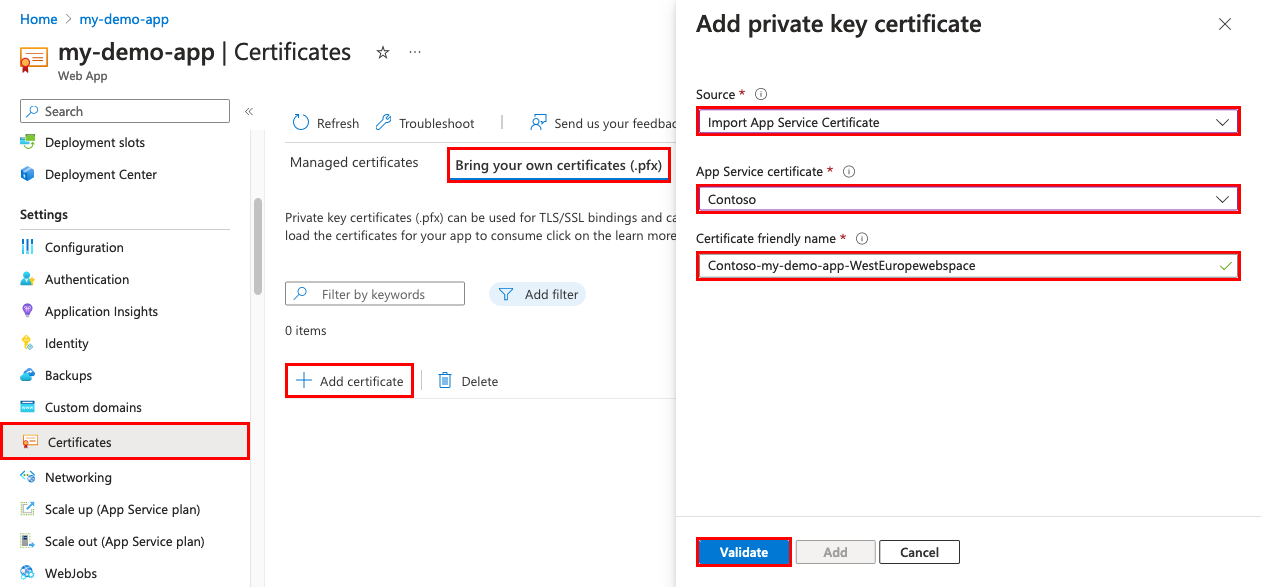
Select the document that yous just purchased and select OK.
When the operation completes, you see the document in the Individual Key Certificates list.
Important
To secure a custom domain with this certificate, you nevertheless need to create a certificate bounden. Follow the steps in Create bounden.
Import a document from Central Vault
If you lot use Azure Fundamental Vault to manage your certificates, you lot tin can import a PKCS12 certificate from Fundamental Vault into App Service as long as it satisfies the requirements.
Authorize App Service to read from the vault
By default, the App Service resource provider doesn't have access to the Key Vault. In order to utilize a Key Vault for a certificate deployment, you demand to authorize the resource provider read access to the KeyVault.
abfa0a7c-a6b6-4736-8310-5855508787cd is the resources provider service chief name for App Service, and it's the aforementioned for all Azure subscriptions. For Azure Government cloud surroundings, use 6a02c803-dafd-4136-b4c3-5a6f318b4714 instead as the resource provider service master name.
Note
Currently, Key Vault Certificate simply supports Key Vault access policy simply not RBAC model.
Import a certificate from your vault to your app
In the Azure portal, from the left carte, select App Services > <app-name>.
From the left navigation of your app, select TLS/SSL settings > Individual Central Certificates (.pfx) > Import Cardinal Vault Certificate.

Use the post-obit table to help you lot select the certificate.
| Setting | Description |
|---|---|
| Subscription | The subscription that the Fundamental Vault belongs to. |
| Fundamental Vault | The vault with the certificate yous desire to import. |
| Certificate | Select from the listing of PKCS12 certificates in the vault. All PKCS12 certificates in the vault are listed with their thumbprints, but not all are supported in App Service. |
When the functioning completes, you run into the document in the Private Key Certificates listing. If the import fails with an fault, the certificate doesn't meet the requirements for App Service.

Note
If you update your document in Key Vault with a new certificate, App Service automatically syncs your document within 24 hours.
Of import
To secure a custom domain with this certificate, y'all however need to create a certificate binding. Follow the steps in Create bounden.
Upload a individual document
Once you obtain a certificate from your certificate provider, follow the steps in this section to make it fix for App Service.
Merge intermediate certificates
If your certificate authorisation gives you multiple certificates in the document chain, you lot need to merge the certificates in club.
To exercise this, open each certificate you received in a text editor.
Create a file for the merged certificate, called mergedcertificate.crt. In a text editor, copy the content of each certificate into this file. The society of your certificates should follow the order in the certificate chain, beginning with your certificate and ending with the root certificate. It looks like the following example:
-----BEGIN Document----- <your entire Base64 encoded SSL document> -----Terminate CERTIFICATE----- -----BEGIN CERTIFICATE----- <The entire Base64 encoded intermediate document 1> -----Finish CERTIFICATE----- -----Begin CERTIFICATE----- <The entire Base64 encoded intermediate certificate 2> -----Cease Document----- -----BEGIN Document----- <The entire Base64 encoded root certificate> -----End Document----- Export certificate to PFX
Export your merged TLS/SSL certificate with the private key that your certificate request was generated with.
If you generated your certificate request using OpenSSL, then you lot have created a private key file. To export your certificate to PFX, run the following command. Replace the placeholders <private-key-file> and <merged-certificate-file> with the paths to your private central and your merged certificate file.
openssl pkcs12 -consign -out myserver.pfx -inkey <private-fundamental-file> -in <merged-certificate-file> When prompted, define an export password. You'll use this password when uploading your TLS/SSL certificate to App Service subsequently.
If you used IIS or Certreq.exe to generate your certificate asking, install the certificate to your local machine, and then export the document to PFX.
Upload certificate to App Service
You're now prepare upload the certificate to App Service.
In the Azure portal, from the left carte, select App Services > <app-name>.
From the left navigation of your app, select TLS/SSL settings > Individual Cardinal Certificates (.pfx) > Upload Certificate.
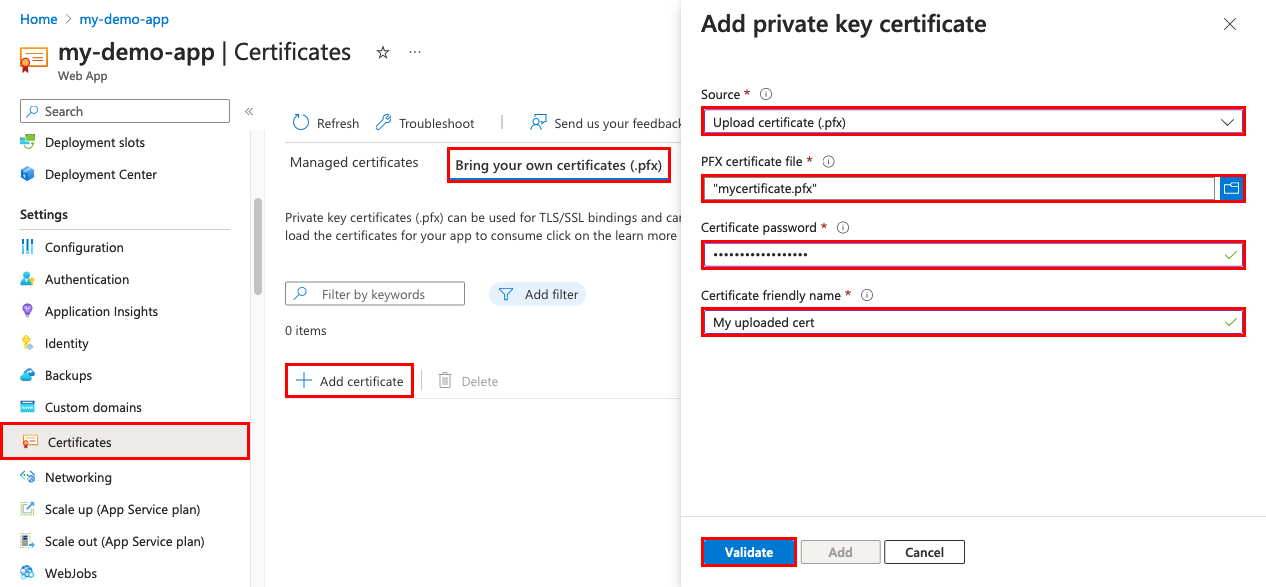
In PFX Certificate File, select your PFX file. In Certificate countersign, blazon the countersign that y'all created when y'all exported the PFX file. When finished, click Upload.
When the operation completes, y'all come across the certificate in the Private Fundamental Certificates list.

Of import
To secure a custom domain with this certificate, you withal need to create a certificate binding. Follow the steps in Create binding.
Upload a public certificate
Public certificates are supported in the .cer format.
In the Azure portal, from the left carte, select App Services > <app-proper name>.
From the left navigation of your app, click TLS/SSL settings > Public Certificates (.cer) > Upload Public Key Document.
In Name, type a name for the certificate. In CER Certificate file, select your CER file.
Click Upload.
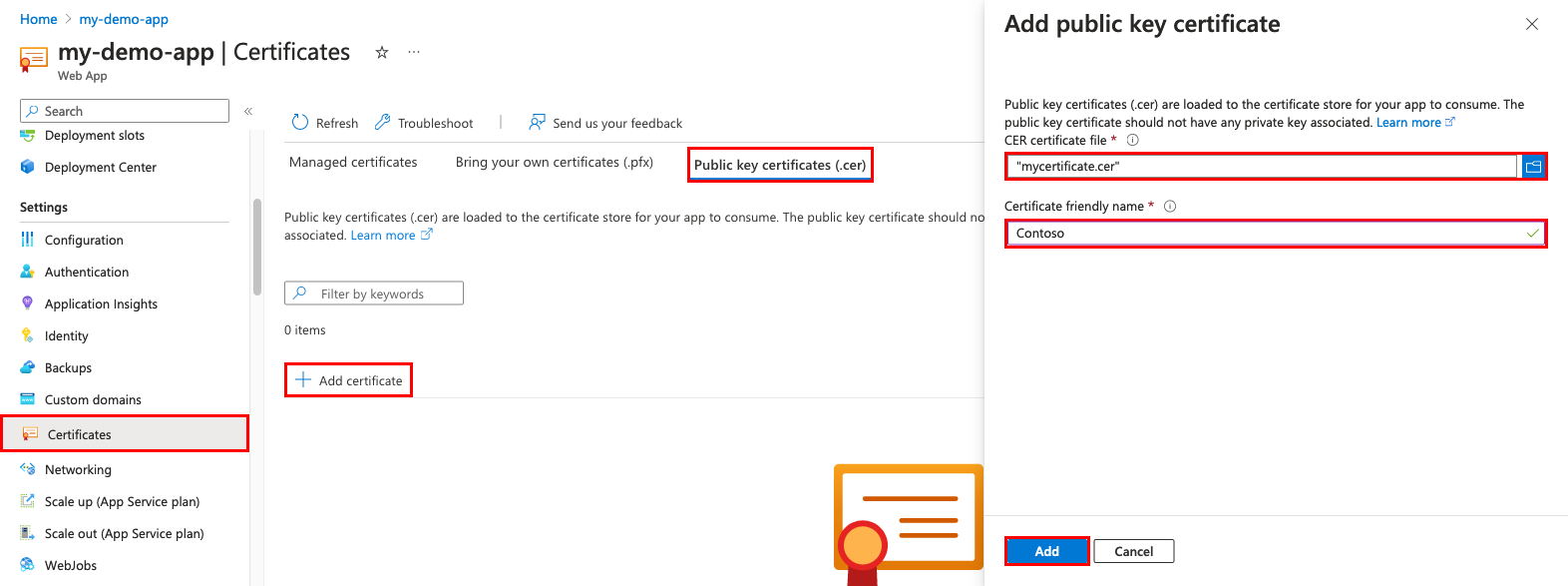
Once the certificate is uploaded, copy the document thumbprint and come across Brand the certificate accessible.
Renew an expiring certificate
Earlier a certificate expires, you should add together the renewed certificate into App Service and update any TLS/SSL binding. The process depends on the certificate type. For example, a certificate imported from Key Vault, including an App Service document, automatically syncs to App Service every 24 hours and updates the TLS/SSL binding when you lot renew the certificate. For an uploaded certificate, there's no automated binding update. See one of the post-obit sections depending on your scenario:
- Renew an uploaded document
- Renew an App Service document
- Renew a document imported from Key Vault
Renew an uploaded certificate
To supervene upon an expiring document, how you update the document binding with the new certificate can adversely affect user experience. For example, your inbound IP address can modify when you delete a binding, even if that binding is IP-based. This is especially important when you renew a certificate that'due south already in an IP-based bounden. To avert a change in your app's IP accost, and to avoid downtime for your app due to HTTPS errors, follow these steps in lodge:
- Upload the new certificate.
- Demark the new certificate to the aforementioned custom domain without deleting the existing (expiring) certificate. This action replaces the bounden instead of removing the existing certificate bounden. To do this, navigate to the TLS/SSL settings bract of your App Service and select the Add Binding button.
- Delete the existing certificate.
Renew an App Service certificate
Note
Beginning September 23 2021, App Service certificates crave domain verification during renew or rekey if you haven't verified domain in the last 395 days. The new certificate gild remains in "pending issuance" during renew or rekey until y'all complete the domain verification.
Different App Service Managed Certificate, domain re-verification for App Service certificates is not automated, and failure to verify domain buying volition result in failed renewals. Refer to verify domain ownership for more than information on how to verify your App Service certificate.
By default, App Service certificates accept a one-twelvemonth validity period. About the time of expiration, App Service certificates, can exist renewed in ane-yr increments automatically or manually. In effect, th renewal process gives you a new App Service certificate with the expiration date extended to one year from the existing document's expiration date.
To toggle the automatic renewal setting of your App Service certificate at whatever time, select the certificate in the App Service Certificates folio, and so click Auto Renew Settings in the left navigation.
Select On or Off and click Save. Certificates tin start automatically renewing 32 days before expiration if you have automatic renewal turned on.

To manually renew the document instead, click Transmission Renew. You can request to manually renew your certificate 60 days before expiration.
One time the renew functioning is complete, click Sync. The sync functioning automatically updates the hostname bindings for the certificate in App Service without causing whatever downtime to your apps.
Annotation
If y'all don't click Sync, App Service automatically syncs your document within 24 hours.
Renew a certificate imported from Central Vault
To renew a certificate you imported into App Service from Key Vault, see Renew your Azure Primal Vault certificate.
Once the certificate is renewed in your fundamental vault, App Service automatically syncs the new certificate and updates any applicable TLS/SSL binding inside 24 hours. To sync manually:
- Go to your app's TLS/SSL settings page.
- Select the imported certificate nether Individual Key Certificates.
- Click Sync.
Manage App Service certificates
This section shows you how to manage an App Service certificate y'all purchased.
- Rekey certificate
- Consign certificate
- Delete document
Also, see Renew an App Service certificate
Rekey certificate
If you retrieve your certificate's private key is compromised, you can rekey your certificate. Select the certificate in the App Service Certificates page, and then select Rekey and Sync from the left navigation.
Click Rekey to start the procedure. This process can take one-ten minutes to complete.
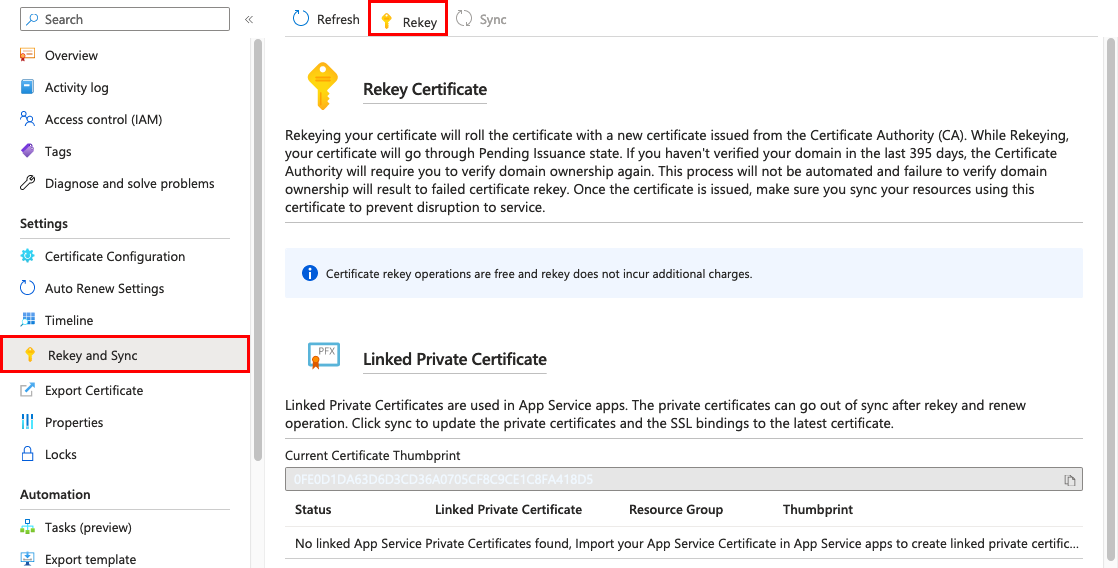
Rekeying your certificate rolls the certificate with a new document issued from the document authority.
You may be required to reverify domain ownership.
Once the rekey operation is complete, click Sync. The sync operation automatically updates the hostname bindings for the certificate in App Service without causing whatsoever downtime to your apps.
Note
If you lot don't click Sync, App Service automatically syncs your document inside 24 hours.
Export certificate
Because an App Service Certificate is a Key Vault secret, y'all can export a PFX copy of information technology and use it for other Azure services or exterior of Azure.
Annotation
The exported certificate is an unmanaged antiquity. For example, it isn't synced when the App Service Certificate is renewed. Yous must export the renewed certificate and install it where you need information technology.
- Azure portal
- Azure CLI
-
Select the certificate in the App Service Certificates folio, then select Export Certificate from the left navigation.
-
Select Open in Key Vault.
-
Select the electric current version of the certificate.
-
Select Download as a certificate.
The downloaded PFX file is a raw PKCS12 file that contains both the public and private certificates, and its import password is an empty string. You tin install it locally by leaving the countersign field empty. Notable is the fact that it can't be uploaded into App Service as-is considering it'southward not countersign protected.
Delete document
Deletion of an App Service certificate is last and irreversible. Deletion of an App Service Certificate resource results in the certificate being revoked. Any bounden in App Service with this certificate becomes invalid. To forbid accidental deletion, Azure puts a lock on the certificate. To delete an App Service certificate, you must starting time remove the delete lock on the certificate.
Select the document in the App Service Certificates page, then select Locks in the left navigation.
Observe the lock on your document with the lock type Delete. To the right of it, select Delete.
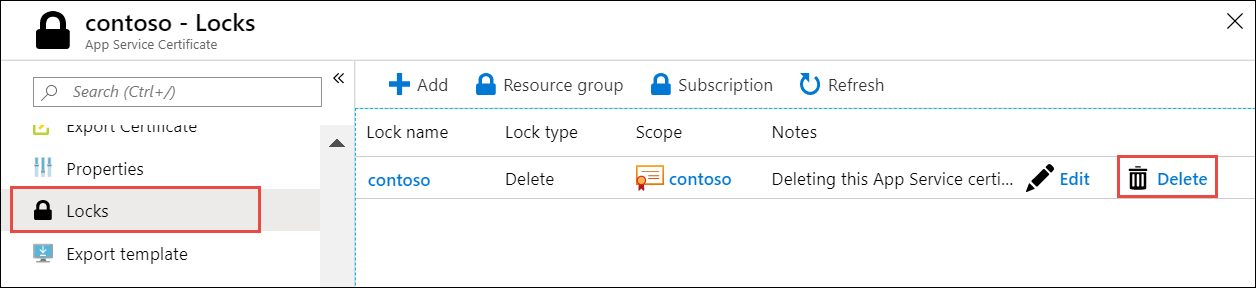
Now you can delete the App Service certificate. From the left navigation, select Overview > Delete. In the confirmation dialog, type the document name and select OK.
Automate with scripts
Azure CLI
Demark a custom TLS/SSL document to a web app
PowerShell
$fqdn="<Replace with your custom domain name>" $pfxPath="<Supercede with path to your .PFX file>" $pfxPassword="<Replace with your .PFX password>" $webappname="mywebapp$(Become-Random)" $location="West Europe" # Create a resource grouping. New-AzResourceGroup -Name $webappname -Location $location # Create an App Service plan in Gratuitous tier. New-AzAppServicePlan -Name $webappname -Location $location ` -ResourceGroupName $webappname -Tier Free # Create a web app. New-AzWebApp -Proper noun $webappname -Location $location -AppServicePlan $webappname ` -ResourceGroupName $webappname Write-Host "Configure a CNAME tape that maps $fqdn to $webappname.azurewebsites.internet" Read-Host "Press [Enter] primal when ready ..." # Before continuing, go to your DNS configuration UI for your custom domain and follow the # instructions at https://aka.ms/appservicecustomdns to configure a CNAME record for the # hostname "world wide web" and bespeak it your spider web app'due south default domain name. # Upgrade App Service programme to Basic tier (minimum required by custom SSL certificates) Fix-AzAppServicePlan -Name $webappname -ResourceGroupName $webappname ` -Tier Basic # Add together a custom domain name to the spider web app. Prepare-AzWebApp -Name $webappname -ResourceGroupName $webappname ` -HostNames @($fqdn,"$webappname.azurewebsites.net") # Upload and bind the SSL document to the web app. New-AzWebAppSSLBinding -WebAppName $webappname -ResourceGroupName $webappname -Name $fqdn ` -CertificateFilePath $pfxPath -CertificatePassword $pfxPassword -SslState SniEnabled More resource
- Secure a custom DNS name with a TLS/SSL binding in Azure App Service
- Enforce HTTPS
- Enforce TLS 1.1/1.two
- Use a TLS/SSL certificate in your code in Azure App Service
- FAQ : App Service Certificates
Feedback
Submit and view feedback for
How To Check If My Https Certificate Is Registered For Both Www And Non Www,
Source: https://docs.microsoft.com/en-us/azure/app-service/configure-ssl-certificate
Posted by: morganforway.blogspot.com


0 Response to "How To Check If My Https Certificate Is Registered For Both Www And Non Www"
Post a Comment